Non-Custodial
A standard requirement for wallets to not become money transmitters is to let purely the owner of the keys compose and transact transactions. While a good implementation significantly reduces the chance of attacker based fund losses, it also increases the chance of user losing funds (due to password or mnemonic key losses). Even though the reputation of non-custodial wallets is to be limited in functionality, most functionalities can be replicated even dissolving the concept.

What does non-custodial actually mean
While the definition states that the users need to be in full control of their funds and in extended version, wallet service providers shall not be fiduciaries of the money, the definition is still wide open. While some wallet providers such as MoneyButton encrypt their Mnemonics with a password (which requires the user to never forget their password, the equivalent is the Relysia Secure Wallet), others go with “keyless solutions”, where the key is fragmented in multiple parts (owned by various providers, equivalent is the Relysia Standard Wallet). The question in both solutions is rather to which degree it is impossible to intrude the users security, but certainly none of the solutions provide any bullet proof security. The question then is, do we define as non-custodial an application based on effort it would take to take custody? (cracking a short password or hacking the client side application/internal structure). One may argue above named steps are basic server security requirements (that face the same dilemma), not specific blockchain or crypto based standard measures. It likely comes rather down to the base operational practices of a wallet infrastructure whether they access keys without permission or not.
Smart Non-Custodial
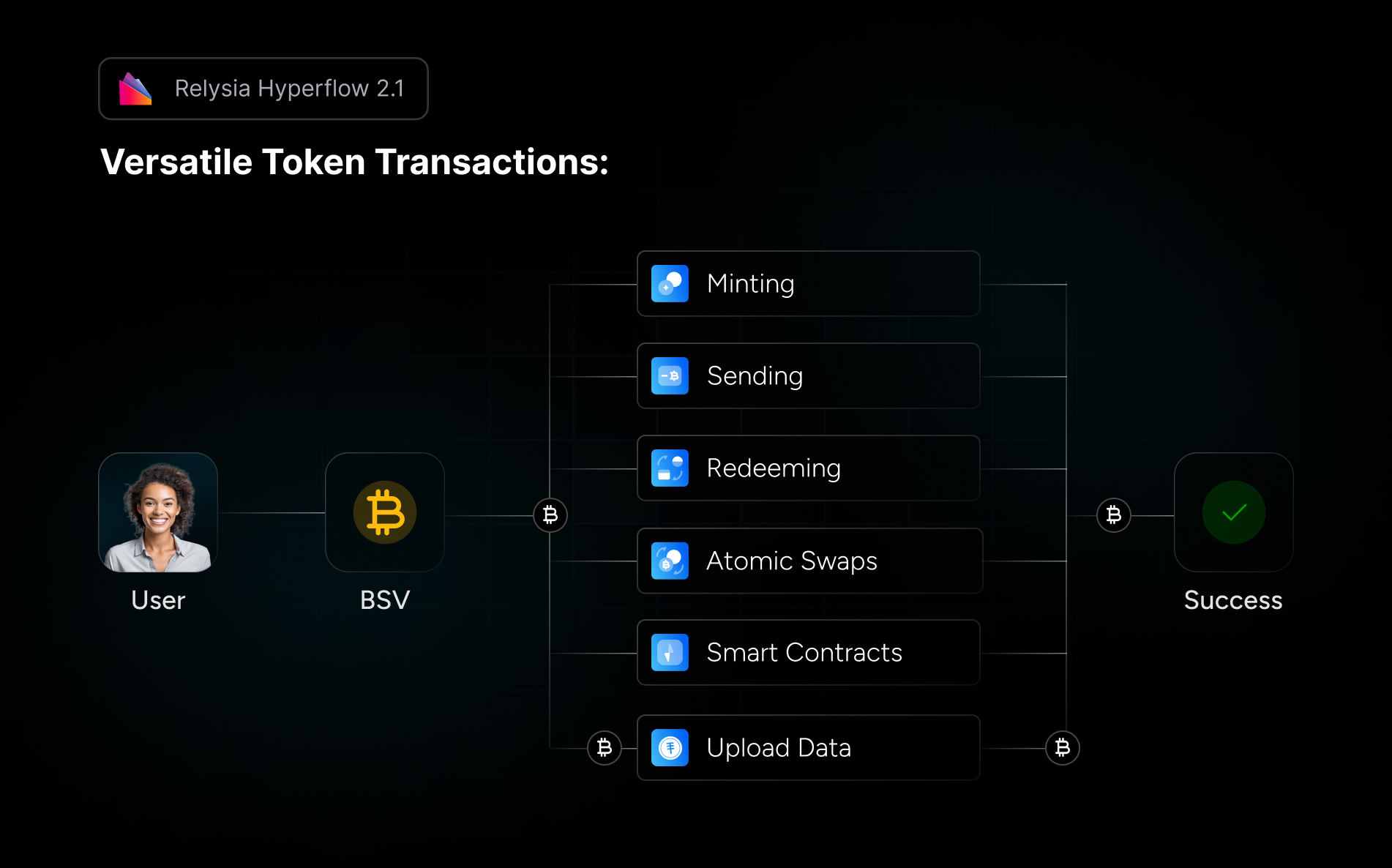
Even without a non-user triggered key usage, there is a wide variety of p2p inspired methods to make full usage of our newly discovered “programmable” money. Transaction bundles can be composed, but not submitted (equivalent to writing a cheque), and thus be used in auctioning mechanisms. Other methods including bitcoin script based atomic swaps to exchange goods (another pre-composed bundle, just in different shape), that are especially attractive in combination with tokenization contracts. We think that different types of non-custodial wallets with different security standards are best suited to offer each client group the best service for their needs. While some users prefer the ease of use, and password reset functionalities of standard wallets, others prefer the higher degree of security with password protected or even multi signature based wallets.
The debate on methods related to creating non-custodian wallets will likely fade over time in the background of blockchain adoption, as regulations are not fine grained enough to create clear definitions. We thus take the user experience first, and let everyone pick the combination of utility and security they require for their individual applications.